IIHT Uganda.
High IT Education Institute.
Skycure, a mobile threat defense solutions, witnessed sudden crash of an iOS app while setting the router in a specific configuration and connecting the devices to it.
Elisha and Roy members of research team started to analyze the crashes
further, and identified the source of the problem. They found that by
generating a specially crafted SSL certificate, attackers can regenerate
a bug and cause apps that perform SSL communication to crash at will.
Then they created a script that exploits the bug over a network
interface.
Parsing SSL certificate vulnerability affects the underlying iOS
operating system, and with heavy use of devices exposed to the
vulnerability, the operating system crashes. Under certain conditions,
the devices can be put into a repeatable reboot cycle, rendering them
useless.
For most of the people iOS app crash is simply a quality issue. They just install a different firmware and move on.
But the victim’s device in an unusable state for as long as the attack
impacts a device. Even if victims understand that the attack comes from a
Wi-Fi network, they can’t disable the Wi-Fi interface in the repeated
restart state as shown in the video.
The issues have been reported to the Apple. To avoid this vulnerability exploit the users may take following steps.
1)Users should disconnect from the bad Wi-Fi network or change their
location in case they experience continuous crashing or rebooting.
2)The latest iOS 8.3 update might have fixed a few of the mentioned
threats–users are highly advised to upgrade to the latest version.
3)In general, users should avoid connecting to any suspicious “FREE” Wi-Fi network.
Posted by :
http://www.ehackingnews.com
IIHT is Asia's No. 1 IT Institute. IIHT Uganda is the best IT Training Institute in Uganda
Wednesday, 29 April 2015
Tuesday, 28 April 2015
Critical SSL Vulnerability Leaves 25,000 iOS Apps Vulnerable to Hackers
 |
| IIHT Uganda |
A critical vulnerability resides in AFNetworking could allow an attacker to cripple the HTTPS protection of 25,000 iOS apps available in Apple's App Store via man-in-the-middle (MITM) attacks.
AFNetworking
is a popular open-source code library that lets developers drop
networking capabilities into their iOS and OS X products. But, it fails
to check the domain name for which the SSL certificate has been issued.
Any Apple iOS application that uses AFNetworking version prior to the latest version 2.5.3 may be vulnerable to the flaw that could allow hackers to steal or tamper data, even if the app protected by the SSL (secure sockets layer) protocol.
Use any SSL Certificate to decrypt users' sensitive data:
An attacker could use any valid SSL certificate for any domain name in
order to exploit the vulnerability, as long as the certificate issued by
a trusted certificate authority (CA) that’s something you can buy for
$50.
"This meant that a coffee shop attacker could still eavesdrop on private data or grab control of any SSL session between the app and the Internet," reports SourceDNA, a startup company that provides code analysis services.
Like, for example, I can pretend to be 'facebook.com' just by presenting a valid SSL certificate for 'thehackernews.com.'
The vulnerability, which is estimated to affect more than 25,000 iOS apps, was discovered and reported by Ivan Leichtling from Yelp.
AFNetworking had fixed the issue in its latest release 2.5.3 before the
previous version 2.5.2, which fails to patch another SSL-related
vulnerability.
Version 2.5.2 Failed to Patch the issue:
Previously it was believed that with the release of AFNetworking 2.5.2,
the lack of SSL certificate validation issue had been eliminated that
allowed hackers with self-signed certificates to intercept the encrypted
traffic from vulnerable iOS apps and view the sensitive data sent to
the server.
However, even after the vulnerability was patched, SourceDNA scanned for
vulnerable code present in iOS apps and found a number of iOS apps
till then vulnerable to the flaw.
Therefore, anyone with a man-in-the-middle position, such as a hacker on an unsecured Wi-Fi network, a rogue employee inside a virtual private network, or a state-sponsored hacker, presenting their own CA-issued certificate can monitor or modify the protected communications.
Apps from Big Developers found to be vulnerable. SERIOUSLY?
A quick check for iOS products with the domain name validation turned
off; the security company found apps from important developers,
including Bank of America, Wells Fargo, and JPMorgan Chase, likely to be
affected.
SourceDNA also said that the iOS apps from top developers such as
Yahoo and Microsoft, meanwhile, remained vulnerable to the
HTTPS-crippling bug.
Prevention against the flaw:
Just to prevent hackers from exploiting the vulnerability, SourceDNA has not disclosed the list of vulnerable iOS apps.
However, the company advised developers to integrate the latest AFNetworking build (2.5.3) into their products in order to enable domain name validation by default.
SourceDNA is also offering a free check tool that could help developers and end users check their apps for the vulnerability.
Meanwhile, iOS users are also advised to check immediately the status of apps they use, especially those apps that use bank account details or any other sensitive information.
And before the developers of vulnerable apps release an update, users
should avoid using any vulnerable version of the apps for the time
being.
Posted by:
www.thehackernews.com/2015/04/ssl-vulnerability-iOS-security.html
For more detail visit this site
Wednesday, 18 March 2015
Monday, 16 February 2015
Thursday, 5 February 2015
How to hack Windows 7 without any software
Step 1 open your computer and set password
Step 2 Then restart computer forcefully with power button
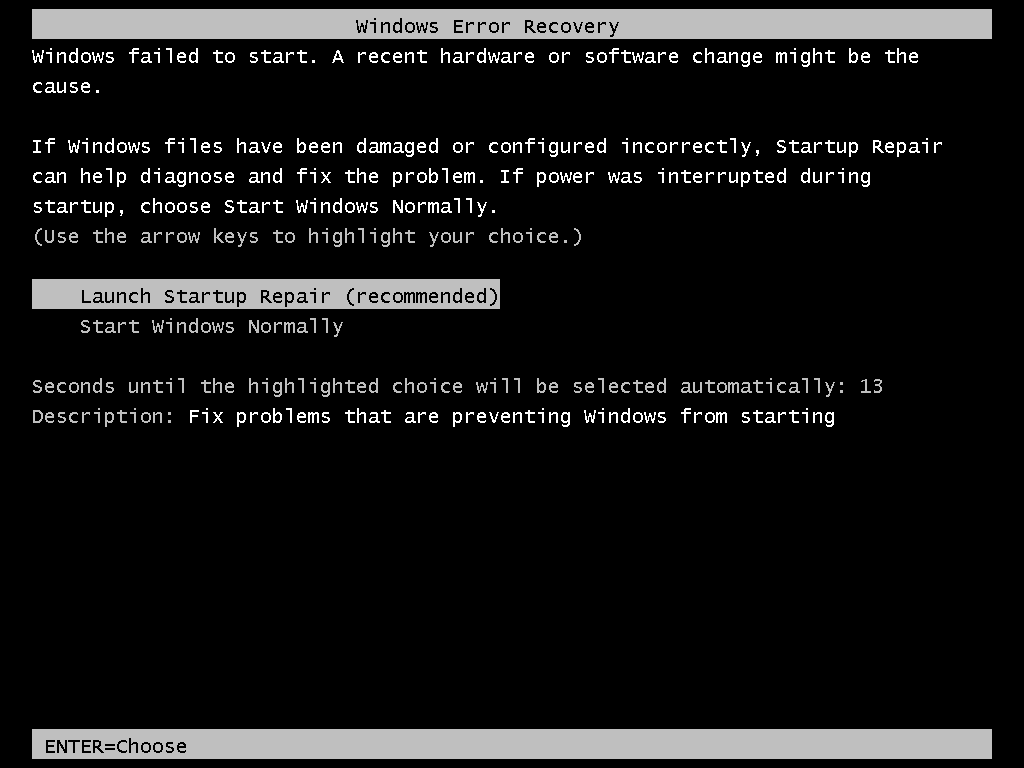
Step 3 You will get this screen for launch repair
Step 6 go to file and click on open it will give you explorer windows
Step 7 go to c drive and find windows/system32
Step 8 change name of CMD.exe and replace with sethc.exe
Step 9 same with sethc.exe with cmd
Step 10 now restart your computer and when u get login screen hit shift key 5 time
Step 11 when you get CMD run command localgroup administrator
Step 12 now run command to change user password which you want net user username /password
Step 13 now you can login in that system with that user
Thanks
source www.techworm.net
Step 2 Then restart computer forcefully with power button
Step 3 You will get this screen for launch repair

Step 4 Let the repair and cancel from the process
Step 5 When you get this window click on show and scroll down and click on a lick it will give you notepadStep 6 go to file and click on open it will give you explorer windows
Step 7 go to c drive and find windows/system32
Step 8 change name of CMD.exe and replace with sethc.exe
Step 9 same with sethc.exe with cmd
Step 10 now restart your computer and when u get login screen hit shift key 5 time
Step 11 when you get CMD run command localgroup administrator
Step 12 now run command to change user password which you want net user username /password
Step 13 now you can login in that system with that user
Thanks
source www.techworm.net
Let
the repair go through. If you get this window, select “Cancel.” - See
more at:
http://www.techworm.net/2015/02/log-administrator-account-windows-pc-image-tutorial.html#sthash.pGFCcKLn.dpuf
Let
the repair go through. If you get this window, select “Cancel.” - See
more at:
http://www.techworm.net/2015/02/log-administrator-account-windows-pc-image-tutorial.html#sthash.pGFCcKLn.dpuf
WARNING:
I am NOT responsible for any expulsions or such if you do this at
school/work! First, restart your computer. - See more at:
http://www.techworm.net/2015/02/log-administrator-account-windows-pc-image-tutorial.html#sthash.pGFCcKLn.dpuf
WARNING:
I am NOT responsible for any expulsions or such if you do this at
school/work! First, restart your computer. - See more at:
http://www.techworm.net/2015/02/log-administrator-account-windows-pc-image-tutorial.html#sthash.pGFCcKLn.dpuf
Subscribe to:
Comments (Atom)
















